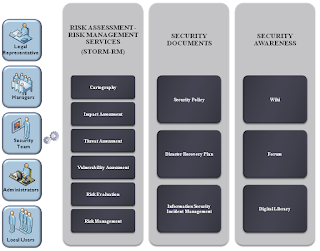
First Revisions to Both Publications in Eight Years
The National Institute of Standards and Technology has published new guidance on malware incident prevention and handling for desktops and laptops as well as enterprise patch management technologies.
NIST Special Publication 800-83 Revision 1, "Guide to Malware Incident Prevention and Handling for Desktops and Laptops," provides recommendations for improving an organization's malware incident prevention measures. The publication also gives extensive recommendations for enhancing an organization's existing incident response capability so that it is better prepared to handle malware incidents, particularly widespread ones. Malware is the most common external threat to most hosts, causing widespread damage and disruption and necessitating extensive recovery efforts.
SP 800-40 Revision 3, "Guide to Enterprise Patch Management Technologies," provides an overview of enterprise patch management technologies. It also briefly discusses metrics for assessing the technologies' effectiveness. The publication is designed to assist organizations in understanding the basics of enterprise patch management technologies. Patch management is the process of identifying, acquiring, installing and verifying patches for products and systems.
NIST also issued SP 800-165, "2012 Computer Security Division Annual Report," which highlights the activities of NIST's Computer Security Division during fiscal year 2012, which ended Sept. 30.
The National Institute of Standards and Technology has published new guidance on malware incident prevention and handling for desktops and laptops as well as enterprise patch management technologies.
NIST Special Publication 800-83 Revision 1, "Guide to Malware Incident Prevention and Handling for Desktops and Laptops," provides recommendations for improving an organization's malware incident prevention measures. The publication also gives extensive recommendations for enhancing an organization's existing incident response capability so that it is better prepared to handle malware incidents, particularly widespread ones. Malware is the most common external threat to most hosts, causing widespread damage and disruption and necessitating extensive recovery efforts.
SP 800-40 Revision 3, "Guide to Enterprise Patch Management Technologies," provides an overview of enterprise patch management technologies. It also briefly discusses metrics for assessing the technologies' effectiveness. The publication is designed to assist organizations in understanding the basics of enterprise patch management technologies. Patch management is the process of identifying, acquiring, installing and verifying patches for products and systems.
NIST also issued SP 800-165, "2012 Computer Security Division Annual Report," which highlights the activities of NIST's Computer Security Division during fiscal year 2012, which ended Sept. 30.