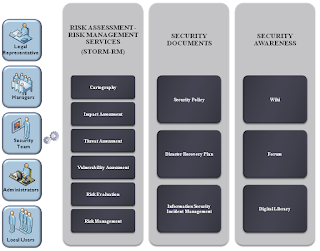
Some questions we need to address before we embark on Information Security Improvement journey!
Edward Snowden’s leaks to the press, we now know that there has been systematic, broad and deep surveillance of online activity at a scale that could not have been previously imagined. Beyond simply snooping, the revelations pointed to infiltration of the hardware and software we rely on to secure our communications.
When it comes to policies and strategies, it’s hard to go past the tried and tested ways of the past. The best way to make a start is by doing SWOT analysis: Strengths, Weaknesses, Opportunities and Threats.
Strengths
Look within your organisation. There are bound to be some really good things happening when it comes to Information Security. For example, you might have a very well-educated workforce that never open unexpected attachments. Or your IT team is very conscious of the potential threats to your business and have solid systems and processes in place to deal with them.
Weaknesses
Over the last 15 years, the focus of security in enterprises has been on vulnerability tracking and making sure that your systems are protected from external attacks. While that’s still important, it should only be one facet of your total security strategy. Have you considered what happens once someone gets past your firewalls and other blocking mechanisms? Or if the attack starts from within?
Give some consideration in your strategy to dealing with attacks once they are in action. Are your people ready to react once there is a breach? Are they across the latest threats and attack vectors?
Perhaps the most often seen security weakness (in our observation) is that managing compliance with the security policy is seen as an annual project that’s executed in order to keep auditors happy.
If that’s the case in your business, look for ways to alter that culture.
Opportunities
Aside from using security as a way to get lots of shiny new gear into your server racks or to justify new services, getting your Information Security right can be a great chance to re-engage IT with the business. Look for ways to turn the security conversation into an opportunity to change service delivery. It’s also a great way to further the professional development of your staff.
If you have some strong skills in data analytics in the business, you might find you can give them a new challenge by engaging them in threat intelligence.
Employing red/blue team exercises regularly doesn’t just improve your security response but can be a great way to add some excitement to how you manage security.
Review existing systems and processes to find the security issues. You might find it becomes an opportunity to ditch an old legacy system that’s costing lots of time and resources to maintain.
Threats
Over the last year, it’s become apparent that the threats of last decade are really just background noise today. Sure, we need to keep our firewalls locked down and end-point protection up to date but what can you do when your hardware is compromised or a nation-state can break through your encryption?
These are real threats today. Stuxnet, back in 2010, compromised a nuclear power plant. It is believed by many that it was part of an attack by one government against another. Today, Snowden’s documents tell us that the NSA can intercept a massive array of data. And not just from enemies but from within friendly states.
Edward Snowden’s leaks to the press, we now know that there has been systematic, broad and deep surveillance of online activity at a scale that could not have been previously imagined. Beyond simply snooping, the revelations pointed to infiltration of the hardware and software we rely on to secure our communications.
When it comes to policies and strategies, it’s hard to go past the tried and tested ways of the past. The best way to make a start is by doing SWOT analysis: Strengths, Weaknesses, Opportunities and Threats.
Strengths
Look within your organisation. There are bound to be some really good things happening when it comes to Information Security. For example, you might have a very well-educated workforce that never open unexpected attachments. Or your IT team is very conscious of the potential threats to your business and have solid systems and processes in place to deal with them.
Weaknesses
Over the last 15 years, the focus of security in enterprises has been on vulnerability tracking and making sure that your systems are protected from external attacks. While that’s still important, it should only be one facet of your total security strategy. Have you considered what happens once someone gets past your firewalls and other blocking mechanisms? Or if the attack starts from within?
Give some consideration in your strategy to dealing with attacks once they are in action. Are your people ready to react once there is a breach? Are they across the latest threats and attack vectors?
Perhaps the most often seen security weakness (in our observation) is that managing compliance with the security policy is seen as an annual project that’s executed in order to keep auditors happy.
If that’s the case in your business, look for ways to alter that culture.
Opportunities
Aside from using security as a way to get lots of shiny new gear into your server racks or to justify new services, getting your Information Security right can be a great chance to re-engage IT with the business. Look for ways to turn the security conversation into an opportunity to change service delivery. It’s also a great way to further the professional development of your staff.
If you have some strong skills in data analytics in the business, you might find you can give them a new challenge by engaging them in threat intelligence.
Employing red/blue team exercises regularly doesn’t just improve your security response but can be a great way to add some excitement to how you manage security.
Review existing systems and processes to find the security issues. You might find it becomes an opportunity to ditch an old legacy system that’s costing lots of time and resources to maintain.
Threats
Over the last year, it’s become apparent that the threats of last decade are really just background noise today. Sure, we need to keep our firewalls locked down and end-point protection up to date but what can you do when your hardware is compromised or a nation-state can break through your encryption?
These are real threats today. Stuxnet, back in 2010, compromised a nuclear power plant. It is believed by many that it was part of an attack by one government against another. Today, Snowden’s documents tell us that the NSA can intercept a massive array of data. And not just from enemies but from within friendly states.
- So, when was the last time you reviewed your security policy?
- Does it take into account new security mitigation techniques?
- Have you adjusted the skills in your business to manage changing attack methods?
- Is security a once-a-year audit activity?